
Importance
In an era where technology plays a role in people’s lives, whether in purchasing goods and services, as well as in communication and conducting business, access to data and data privacy are therefore issues that must be given importance. Due to the current cyber threats, which arise in many different forms and result in damage to both the individual and business operations, businesses should prepare to prevent such disasters.
“Digital Driven Organization” is one of the OR’s commitments by using technology and digital platforms to conduct its business, support the Online to Offline (O2O) services for business flexibility to respond to the consumers and customers in a timely manner. It also is aware of the risks of business operations that might be related to Data Security and Privacy, such as Malware Phishing, which is classified as one of the Cyber Threats that may cause damages to both the business operations and the company’s reputation. Therefore, effective management of data security and privacy is required to meet the expectations of the customer, and to deliver value to all stakeholder groups through quality and safe products and services.
Target 2023
Management guidelines
OR emphasizes and focuses on managing work in accordance with the Personal Data Protection Act 2019 (PDPA) and secondary laws issued under the Act. Therefore, it has created the Data Privacy Policy of the Company, which includes the Company’s internal structure, policies, and practices related to personal data protection. It applies to all operations of the Company including employees, suppliers, operators, contractors, agents, representatives, directors, executives, as well as other types of personnel of the Company.
OR therefore prepared a privacy policy and categorized it according to utilization of the stakeholder groups into the following 4 groups
- Business Partner Privacy Policy
- Customer Privacy Policy
- Human Resources Privacy Policy
- Internal Privacy Policy, which consists of various sub-policies relating to the entire operations within the OR.
For all these privacy policies, OR meticulously plans and designs the privacy policy notification process, ensuring that appropriate consent is obtained for each stakeholder group.
[Learn more about PR’s privacy policy OR click: https://pdpa.pttor.com/]
Throughout all these comprehensive privacy policies, OR has demonstrated a commitment to handling sensitive information with diligence, covering both internal and external personal privacy aspects, which include own operations, suppliers, and customers across various businesses. This aims to create security and the privacy of personal information and ensures that the OR collects, uses, and discloses information appropriately, in a way that meets the purpose stated to the personal data owner.
In addition, OR also sets the Information Policy. It is a policy on confidentiality, data retention, and usage of inside information. It also sets the OR Enterprise Data Governance policy to establish management directions and support safe information and communications that are in accordance with the needs of the business and relevant laws and regulations for all employees. (An information security/cybersecurity policy is internally available to all employees). This includes a Digital Standards manual for OR, which includes comprehensive content on digital operations such as the Information Security Incident Management, Information Security Aspects of Business Contiguity: BCM, etc.
OR has created additional policies and processes, such as the Consent Management process, Data Retention Standard, Incident Response Procedure for personal data breach, Data Security Incident Reporting and Response Policy, Record of Processing Activities, and Guidance on Data Protection Officer Representative, etc.
Data Security and Privacy Governance
The governance structure is based on the Three Lines Model. This is to facilitate control, supervision and audit functions, with clear Segregation of duty. This is done by the Enterprise Risk Management Committee (ERMC) overseeing the Cybersecurity and Information Technology Security Strategy. OR has appointed the OR Digital & Data Governance Steering Committee (DGSC), which has the Senior Executive Vice President of Corporate Strategy and Sustainability as a committee chairman’s and Chief Information Security Officer (CISO) with responsibility to establish and maintain information technology and digital vision, strategy, and policy to be in line with OR and OR Group policy, direction and business strategy.
Data Security and Data Privacy Governance Structure
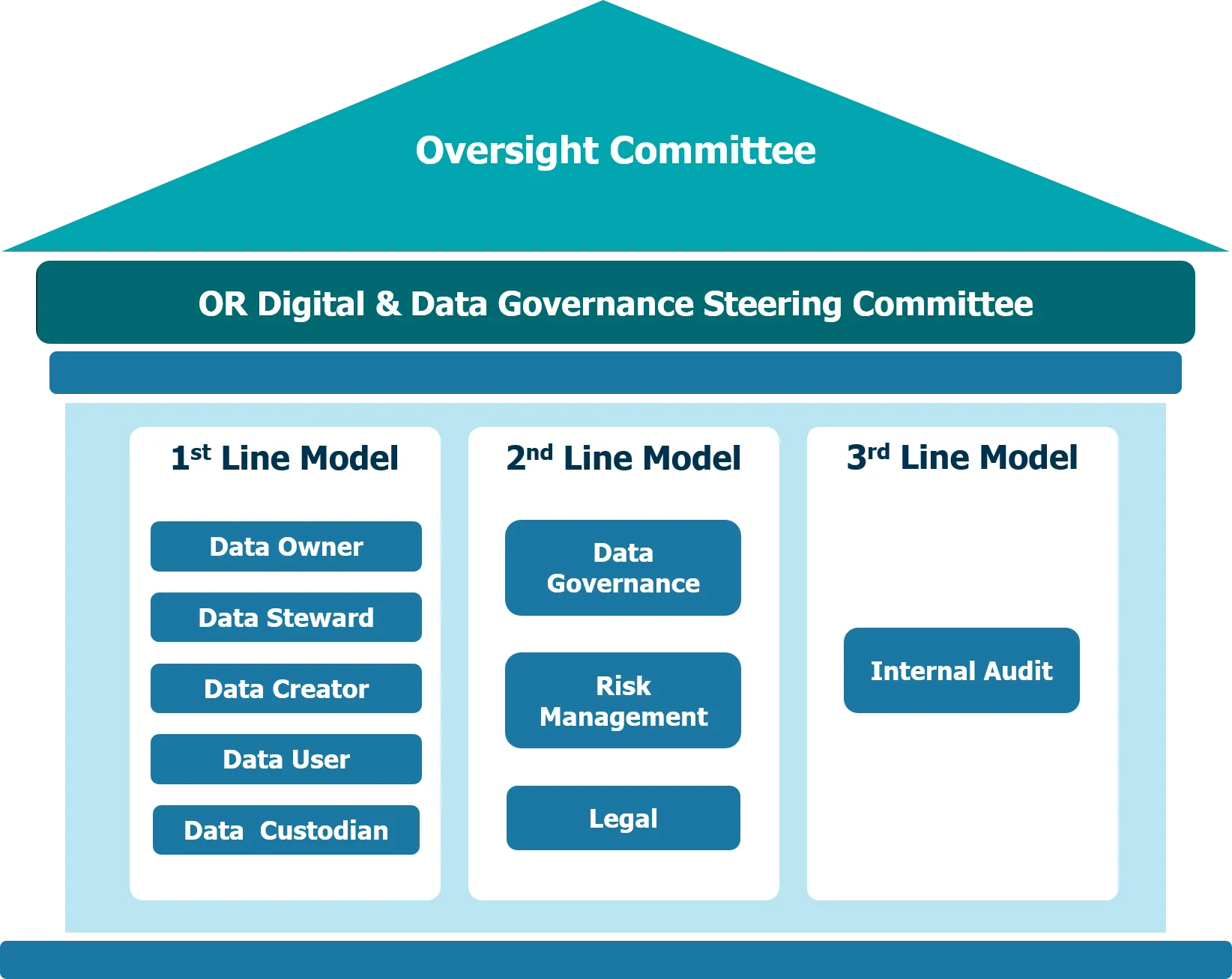
Level | Committee/Department | Responsibility |
Board Level | Enterprise Risk Management Committee | – Supervise in Cybersecurity and Information Technology Security Strategy |
Executive Level and Management Level | OR Digital & Data Governance Steering Committee (DGSC) OR Management Committee (ORMC) | – Set policies, goals and strategies for information technology and digital technology to comply with the business strategic plan of OR and OR Group. |
Operation Level | Data Protection Officer (DPO) | – Provide advice on operations in accordance with personal data protection guidelines. |
OR has appointed Senior Executive Vice President, Corporate Strategy and Sustainability to chair the Digital and Data Governance Committee.
OR has a clear escalation process which employees can follow in the event an employee notices something suspicious is in place. OR provides a Point of Contact regarding data security, privacy, and cybersecurity. It will have a clear way to notification and report of incidents. Employees can acknowledge and follow the method of notifying such incidents in the event that they encounter such an incident that poses a risk to the responsible department without any delays when such an incident occurs. The responsible person has the duty to report incidents to the management or related parties for acknowledgement, and for it to be analyzed and have its risk management to be at an acceptable level. This is to be under the organization’s risk management framework.
Internal audit on the compliance with company’s Privacy Policy is conducted in 2023, to ensure compliance with the policies, standards, and procedures that relates to data governance. The audit shall be carried out at random, taking into account the pool of personal data subjects, and of the activities in which personal data is processed on a large scale.
For the policy compliance, following OR’s Corporate Governance, Ethical Standards and Code of Business Ethics Handbook, OR personnel must comply with Information Technology security requirements, Information Technology security management policy, cyber security policy, and other related policies of the Company.
Risk Assessment and Identification
OR conducts a Data Processing Impact Assessment by processing data that is a risk to the rights and freedoms of the personal data owner. It also sets the measures to reduce the impact to reach acceptable levels. In addition, the OR specifies the Key Risk Indicator: KRI on the topic of IT Infrastructure Instability and Cybersecurity. This is for systematic performance monitoring and ensuring that the business has a surveillance and that it monitors risks that may arise from data security and privacy issues.
Records of Processing Activities are maintained by all departments as a database of each department and the organization that are involved in personal data. This makes it easy to follow and verify accuracy in accordance with the right purpose for usage. This also includes accordance with relevant legal bases. The Records of Processing Activities are conducted according to the requirements of the Personal Data Protection Act of 2019.
Data security, privacy, and cybersecurity
Committed to conducting business under the concept of Digital Driven Organization, OR is prepared for risks arising from security, data privacy, and cyber threats. OR complies with ISO/IEC 27001:2013 standards and the cyber security framework developed by National Institute of Standards and Technology (NIST). It starts from the installation of Perimeter Protection, or the installation of a Firewall, which is a filter for traffic before it enters the computer or network within the organization from the internet or from other sources of attack. This also includes Data Encryption, converting data to be a secret code that will help keep data safe for the Hardware and Software.
There is also Authentication and Authorization management and controls for data access to be limited. There are Account Username Password that are managed separately. This is so that it can be traceable from the Log in cases of data breach. It also uses Two-Factor Authentication in accessing data that are important. The DLP or Data Loss Prevention Solution is used for monitoring and analyzing sensitive data export out of the organization in accordance with the Data Classification policy. Enterprise-level security done by using international standard Antivirus Software to ensure the security of data for various devices.
OR’s customer security and privacy has a clear policy. This is in line with the Personal Data Protection Act (PDPA). OR sets cookies to store or track information about the use of websites, and to analyze the Trend. Website management will track the website visit of the user to remember the user’s preferences. In this regard, the OR has a tracking record of customer data usage, in accordance with the announced customer privacy policy and also, in order to comply with the Computer-Related Crime Act B.E. 2550 (2007) as amended by the Computer-Related Crime Act (No.2) B.E. 2560 (2017), section 26.
To ensure that the information systems developed or updated have been tested for safety, OR has procedures for Security Testing, and has an external agency test the information security system. This is done by simulating the computer network hacking situation or vulnerability analysis to OR. Penetration Testing is one example. In addition, OR has developed a Disaster Recovery Plan as a guideline for executives and related parties to know their roles, duties, and procedures for operations in the event of a threat to security and data privacy. OR has the Information Security of Business Continuity Management. It will examine the information security continuity measures that have been established and the results of their implementation, which are reviewed annually.
Audits for compliance with the OR’s personal data security policy and cybersecurity are done by Internal Auditors as well as third-party audit annually. This is in accordance with the ISO 27001:2013.
The results of operations related to data security and privacy, as well as cybersecurity is recorded and analyzed for the possibility of improving the security and data privacy management system, as well as specifying a plan for future business operations.
Overall of internal audit conducted in 2023 for personal data protection operations is complied with principles and requirements of the Personal Data Protection Act B.E. 2562 (2019), sub-regulations (notifications), and other relevant announcements. The inspection is categorized into two aspects: legal preparation and personnel and organization’s procedure preparation. The main topics are as follows:
- Obtaining consent
- Processing of personal data (Collection, Use, Disclosure of Personal Data)
- Notification of details and objectives to the data subject
- Baseline used for data processing
- Sending or transferring data abroad
- Data Subject Rights
- Duties of the data controller
- Recording of personal data processing activities
- Duties of data processors / contracts for processing personal data
From the audit, it was found that OR has prepared itself so that the organization, personnel, and related processes can conduct business appropriately in accordance with legal requirements. OR has an annual internal audit plan to ensure that the organization can conduct business in accordance with the aforementioned relevant laws.
Complaint Channel
OR has a complaint channel in the event of leak of personal information, through the 1365 Contact Center, or through the email dpo@pttor-staging.livetubex.com The Complaints will be reported to the Data Protection Officer (DPO). The relevant departments will acknowledge the information, and it will be analyzed and prepared to have a plan to correct and remedy the incident appropriately, as stated in the Incident Response Procedure.
In the event that OR discovers a leak of personal information, OR must report the data breaches, as stipulated in the Personal Data Protection act of 2019. This includes violations that have a high risk of affecting the rights and freedoms of the individual. The remedy guidelines must also be informed without delay and must be notified to the office of the Personal Data Protection Commission.
Performance
To raise awareness of personal data protection (Data Security) and strengthen knowledge of Cybersecurity in the company, the OR has organized training for new employees, to understand the provision of digital services, policies, rules, regulations, practices, and standards for maintaining security of information for the company. This also includes the understanding of laws related to the Computer Crimes Acts, threats, and consequences of misuse and improper use of information systems.
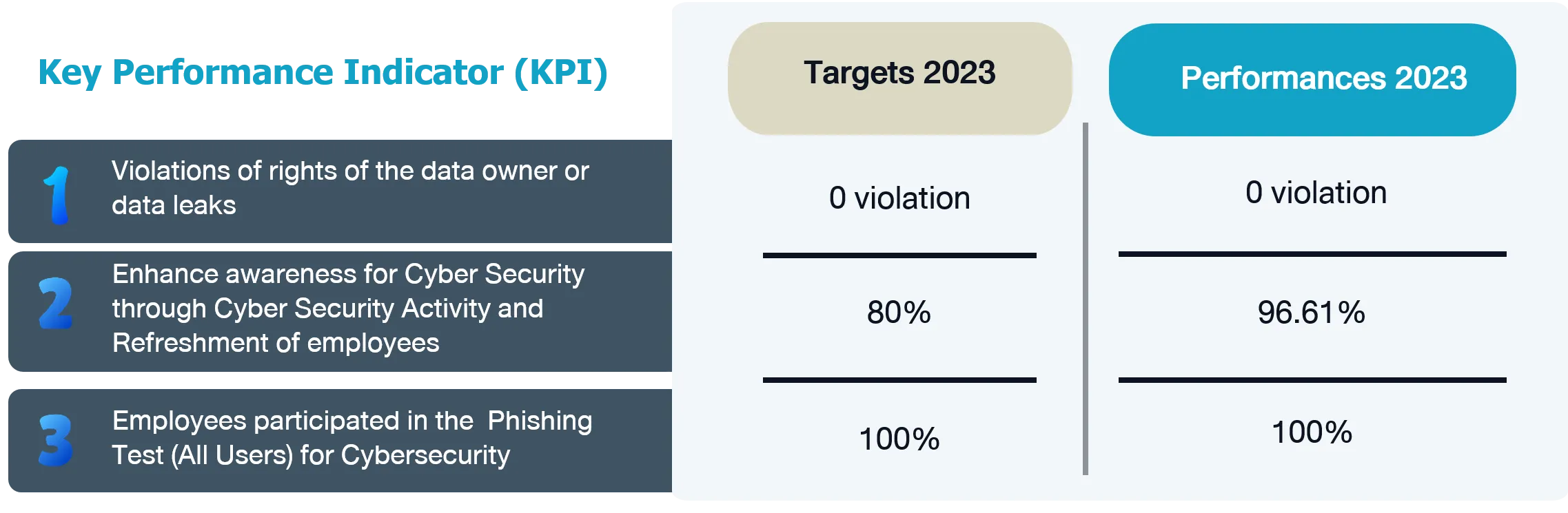
Training content includes topics such as Password Security, Phishing E-mail, Malware Protection, Internet Using Security, etc., which are presented in the form of Animation to add interest to the content. There is also a Refreshment course, which is a Cyber Security Awareness exam for employees who have been working with the Company for a certain amount of time, in order to review and create awareness of the information security management policy. in 2023, 96.61% of participants passed the exam.

Cyber Security Awareness Refreshment
Overall of security and data privacy management in 2023 OR has not encountered any incidents of customer privacy violations and loss of customer data.
In 2023, OR did not receive any reports of complaints of customer privacy violations and loss of customer data for secondary purposes.


